China uses DNS spoofing to block access to websites and prevent connections to VPN servers. This can be prevented by securing your DNS with DNSCrypt.
What is DNS?
Client Implementations. Client Implementations Search. DNSCrypt, DoH and Anonymized DNSCrypt Rust.
DNS stands for Domain Name Systems. It is like a “phonebook for the internet”.
When you use the internet, you do so through domain names. For example, the domain name of this website is tipsforchina.com. While humans use domains names, computer networks use IP addresses. DNS is the system that converts domain names into IP addresses.
What is DNS spoofing?
DNS spoofing (also known as DNS poisoning) is one of the methods that China uses to censor the internet. This happens when a DNS query returns the incorrect IP address for the website or service you are trying to access. The problem with standard DNS requests is that they are sent in plain text (without encryption). So even if you use custom DNS servers (Google, Cloudflare, etc) instead of your ISP DNS servers, DNS spoofing will still happen.
Here is an example.
When I ping the domain name openvpn.net in China, my DNS request returns the IP address 66.220.149.18.
- The Umbrella roaming client runs as a local service which is used as a local resolver and DNS forwarder, encrypting and authenticating requests using the DNSCrypt protocol. Requests are then forwarded to Umbrella’s anycast IPs, with the replies returned to the host through the loopback interface.
- Windows front end for DNSCrypt Proxy. Contribute to opendns/dnscrypt-win-client development by creating an account on GitHub.
- @rotblitz my router nor my devices support DNSCrypt. I see OpenDNS provides a DNSCrypt client for Windows, but what about Android, IOS, AsusWRT (Router), Roku, my many IoT devices, etc? That's just not a feasible solution in my opinion. The router needs to support whatever the DNS security mechanism is, in order for it be useful.
However, this is not the real IP address for the openvpn.net website. In fact, this IP address belongs to Facebook. This kind of DNS spoofing often returns IP addresses that belong to Facebook and Twitter, which are blocked IPs (more on this later).
How does DNSCrypt work?
DNSCrypt is a protocol that prevents DNS spoofing by encrypting and authenticating the communications between a DNS server and client.
Here is the result of my ping to the openvpn.net server after installing Simple DNSCrypt on my computer.
This time, the correct IP address for the openvpn.net domain name is returned.
Can DNSCrypt be used to access blocked websites in China without a VPN?
Usually not, but sometimes.
Unfortunately, DNS spoofing is not the only method that China uses to block websites. The other method is IP blocking. So even if your DNS request returns the correct IP address, the IP address itself will likely be blocked anyway.
You certainly won’t be able to access Google, Facebook, Twitter, or other major websites with well known IP ranges. To get full access to all websites and services, you need to use a VPN service that works well in China.

Having said that, there are a few blocked websites that you can access without a VPN by using DNSCrypt. These are mostly smaller websites that are probably not worth the time of the censors to keep up with blocking their IP addresses.
At the time of writing this article, I was able to access the following websites in China without a VPN by using DNSCrypt (this may be subject to change if the IP addresses of these sites get blocked in the future).
OpenVPN (VPN software for the OpenVPN protocol)
Duck Duck Go (privacy focused search engine)
Tor Project (download page for the Tor browser)
Surfshark (main website of Surfshark VPN)
VPN.ac (main website of VPN.ac)
What else can DNSCrypt be used for?
The main advantage of DNSCrypt is that it can help with connecting to a VPN. VPN servers often use hostnames (similar to domain names) instead of IP addresses in the configuration files.
For example, I was unable to connect to a certain Surfshark VPN server when using the manual OpenVPN config with the OpenVPN app because the DNS request for the server name was not returning the correct IP. After enabling DNSCrypt, I was able to connect successfully.
As in the case with accessing websites, your mileage may vary with this trick. Often, when you can’t connect to a VPN server, the IP address of that server is IP blocked. But sometimes only the hostname used to look up the IP is blocked.
How to install Simple DNSCrypt on Windows
DNSCrypt is just a protocol, not a specific software. There are various software implementations for different platforms. The easiest client implementation for Windows is Simple DNSCrypt.
If you use Mac, you can check the list of DNSCrypt client implementations and try one that supports Mac.
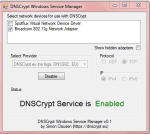
After installing Simple DNSCrypt for Windows, you can launch the application and enable these 2 settings.
Turn on the switch to enable the DNSCrypt Service and then click on your Network card (WiFi or LAN) at the bottom.
I suggest leaving the other settings as default unless you know what you are doing.
If you want to disable DNSCrypt, make sure that you click on your network card again (WiFi or LAN) to disable the DNS settings for that card before you exit the application. Do not disable the DNSCrypt service and leave your network card selected. This will leave your network card DNS settings as 127.0.0.1 and cause your internet to stop working after the service is disabled.
DNSCrypt alternative for Android 9
Android 9 supports DNS over TLS, which is another kind of encrypted DNS system.
The specific steps to find this setting will depend on what phone you are using. For my Samsung Galaxy S8+, it can be found here.

Settings > Connections > More connection settings > Private DNS
Select Private DNS provider hostname and then enter the hostname for a DNS provider that supports DNS over TLS. For example, 1dot1dot1dot1.cloudflare-dns.com or dns.quad9.net.
Dnscrypt-proxy Dnscrypt Client Proxy
Don't let Google see all your DNS traffic. Discover privacy-centric alternatives to the traditional DNS providers.
| DNS Provider | Server Locations | Privacy Policy | Type | Logging | Protocols | DNSSEC | QNAME Minimization | Filtering | Source Code | Hosting Provider |
|---|---|---|---|---|---|---|---|---|---|---|
| AdGuard | Anycast (based in Cyprus) | Commercial | Some | DoH, DoT, DNSCrypt | Yes | Yes | Based on server choice | Choopa, LLC, Serveroid, LLC | ||
| BlahDNS | Finland, Germany, Japan Singapore | Hobby Project | No | DoH, DoT , DNSCrypt | Yes | Yes | Ads, trackers, malicious domains Based on server choice only for DoH | Choopa, LLC, Hetzner Online GmbH | ||
| Cloudflare | Anycast (based in US) | Commercial | Some | DoH, DoT | Yes | Yes | Based on server choice | ? | Self | |
| CZ.NIC | Czech Republic | Association | No | DoH, DoT | Yes | Yes | ? | ? | Self | |
| Foundation for Applied Privacy | Austria | Non-Profit | Some | DoH, DoT | Yes | Yes | No | ? | IPAX OG | |
| LibreDNS | Germany | Informal collective | No | DoH, DoT | Yes | Yes | Based on server choice only for DoH | Hetzner Online GmbH | ||
| NextDNS | Anycast (based in US) | Commercial | Based on user choice | DoH, DoT, DNSCrypt | Yes | Yes | Based on server choice | ? | Self | |
| NixNet | Anycast (based in US), US, Luxembourg | Informal collective | No | DoH, DoT | Yes | Yes | Based on server choice | FranTech Solutions | ||
| PowerDNS | The Netherlands | Hobby Project | No | DoH | Yes | No | No | TransIP B.V. Admin | ||
| Quad9 | Anycast (based in US) | Non-Profit | Some | DoH, DoT, DNSCrypt | Yes | Yes | Malicious domains | ? | Self, Packet Clearing House | |
| Snopyta | Finland | Informal collective | No | DoH, DoT | Yes | Yes | No | ? | Hetzner Online GmbH | |
| UncensoredDNS | Anycast (based in Denmark), Denmark, US | Hobby Project | No | DoT | Yes | No | No | ? | Self, Telia Company AB |
A validating, recursive, caching DNS resolver, supporting DNS-over-TLS, and has been independently audited.
A DNS proxy with support for DNSCrypt, DNS-over-HTTPS, and Anonymized DNSCrypt, a relay-based protocol that the hides client IP address.
An application that acts as a local DNS-over-TLS stub resolver. Stubby can be used in combination with Unbound by managing the upstream TLS connections (since Unbound cannot yet re-use TCP/TLS connections) with Unbound providing a local cache.
Firefox comes with built-in DNS-over-HTTPS support for NextDNS and Cloudflare but users can manually use any other DoH resolver. Warning
Android 9 (Pie) comes with built-in DNS-over-TLS support without the need for a 3rd-party application. Warning
An open-source Android client supporting DNS-over-HTTPS and DNS-over-TLS, caching DNS responses, and locally logging DNS queries.
An open-source iOS client supporting DNS-over-HTTPS, DNSCrypt, and dnscrypt-proxy options such as caching DNS responses, locally logging DNS queries, and custom block lists. Users can add custom resolvers by DNS stamp.
Apple's native support
In iOS, iPadOS, tvOS 14 and macOS 11, DoT and DoH were introduced. DoT and DoH are supported natively by installation of profiles (through mobileconfig files opened in Safari). After installation, the encrypted DNS server can be selected in Settings → General → VPN and Network → DNS.
- Signed profiles are offered by AdGuard and NextDNS.
- User contributed unsigned profiles for several DNS providers are hosted by encrypted-dns.party.
Definitions

DNS-over-TLS (DoT)
A security protocol for encrypted DNS on a dedicated port 853. Some providers support port 443 which generally works everywhere while port 853 is often blocked by restrictive firewalls.
DNS-over-HTTPS (DoH)
Similar to DoT, but uses HTTPS instead, being indistinguishable from 'normal' HTTPS traffic on port 443 and more difficult to block. Warning
Dnscrypt Osx Client
DNSCrypt
Dnscrypt Client Proxy
With an open specification, DNSCrypt is an older, yet robust method for encrypting DNS.
Dnscrypt Client Ubuntu
Anonymized DNSCrypt
Dnscrypt-proxy Max_clients
A lightweight protocol that hides the client IP address by using pre-configured relays to forward encrypted DNS data. This is a relatively new protocol created in 2019 currently only supported by dnscrypt-proxy and a limited number of relays.